From Frontiers in Education, San Diego, October 2006
Embedding Ethics in Computer Architecture
Alan Clements. School of Computing, University of Teesside, Middlesbrough TS1 3BA, UK
Abstract -
Index Terms – Computer science education, Curriculum development, Ethics, Professional issues.
Ethics and the Curriculum
Organizations such as the IEEE Computer Society and accrediting agencies require computer science students to be aware of professional and ethical issues. The Joint CS/ACM Computing Curriculum 2001 very clearly states the requirements for a professional dimension in the curriculum by stating, “Undergraduates also need to understand the basic cultural, social, legal, and ethical issues inherent in the discipline of computing. They should understand where the discipline has been, where it is, and where it is heading. They should also understand their individual roles in this process, as well as appreciate the philosophical questions, technical problems, and aesthetic values that play an important part in the development of the discipline.[1]
Students also need to develop the ability to ask serious questions about the social impact of computing and to evaluate proposed answers to those questions. Future practitioners must be able to anticipate the impact of introducing a given product into a given environment. Will that product enhance or degrade the quality of life? What will the impact be upon individuals, groups, and institutions?
Finally, students need to be aware of the basic legal rights of software and hardware
vendors and users, and they also need to appreciate the ethical values that are the
basis for those rights. Future practitioners must understand the responsibility that
they will bear, and the possible consequences of failure. They must understand their
own limitations as well as the limitations of their tools. All practitioners must
make a long-
Some universities provide complete courses in ethics and professional issues. However,
not every student taking such a course will engage with the notion of ethics. If
the course is taught too early in a student’s curriculum, he or she may not be able
to relate it to their chosen profession. On the other hand, some students will regard
a course in ethics and professional issues as just another hurdle to overcome on
the way to a degree. Some universities do not teach ethics explicitly, but claim
to distribute ethics throughout the curriculum. There is anecdotal evidence that
not all teachers really do follow this practice; that is, lip-
Teaching, Learning and Attention Span
It is said that students learn surprisingly little during formal lectures [2]. Certainly,
any teacher will tell you that many of their students learn only when they are in
problem-
However, we should not simply abandon all lectures and just give up because conventional lectures have been shown to be inefficient. There’s a lot we can do; for example, we can put the student at the center of the learning process by promoting active learning. In this paper I discuss how a form of active learning can have significant advantages in a computer architecture class by providing a forum for discussions on professional issues.
I teach computer architecture in a department where all the other courses are software-
When many of the students are obliged to take my course as part of their core material,
a straight hour of solid lecturing can be painful for the students, demoralizing
for the teacher, and largely a waste of time. Of course, I try and engage the students
in a two-
As well as involving students in the lecture by creating a dialog, I use a break or aside between sections of the lecture to give the students a rest; the effect of the break is to reset the atmosphere and lighten the mood.
A break may consist of little more than a light-
Maintaining Student Attention
Students have a lot to learn while at university and they often find the burden difficult to bear. Anyone who has ever taught undergraduates will be familiar with the cry, “But, is this going to be in the exams?” All too often a student’s attention is proportional to the probability that a topic will appear as exam questions. It is vitally important to get students into the habit of learning and to help them appreciate that passing exams is only a milestone on their path to a profession and not a goal in itself.
One of the first elements of embedded ethics that I introduce is concerned with student motivation. Motivation, as such, is not a component of traditional professional codes of practice, although the British Computer Society, BCS, stresses your duty to both your client and to society.
Motivation is at the heart of professional conduct; an engineer who is motivated
is more likely to succeed than one who is not. I try and increase a student’s desire
to learn more than the minimum necessary to pass the exam, by describing situations
where people extricated themselves from difficult or dangerous situations because
they applied their knowledge in a way that went beyond the bounds of the curriculum.
My motivational asides are often taken from the world of aviation – partly because
I am a pilot myself and partly because students can relate to dramatic life-
I sometimes tell my students the true story of a light aircraft, a Cessna, that was
hopelessly lost over the Pacific Ocean without any navigation equipment as sunset
was approaching. It was highly probable that he would have to ditch in the Pacific
with little chance of being picked up, even if he survived the ditching. For all
practical purposes, the Cessna pilot had only a VHF (line-
An Air New Zealand DC10 picked up his distress call and the captain decided to hunt for the light aircraft – without any obvious means of locating it [3].
At this stage, I ask my students, “What do you think the DC10 captain did?” Invariably, they are completely clueless; even pilots are not taught what to do in such a situation. I explain how the Air New Zealand captain went back to first principles (the purpose of this aside is to demonstrate how going back to basic principles can help you solve a problem that you have never encountered before).
The DC10 captain turned his aircraft to face the sun and asked the lost pilot to do the same. The DC10 reported the direction of the sun as 270º and the Cessna gave a bearing of 274º. This meant that the Cessna was to the south of the DC10, but it didn’t tell the DC10 captain whether the Cessna was to his east or west. So, the DC10 asked the Cessna pilot to hold his hand out and say how many fingers the sun was above the horizon. The DC10 captain measured the sun two fingers above the horizon and the Cessna saw it four fingers above the horizon. If you think about it, the higher the sun in the sky, the closer it is to noon so the local time for the DC10 was later than the Cessna’s local time. This put the Cessna to the west of the DC10.
FIGURE 1 LOCATING AN AIRCRAFT USING VHF RADIO
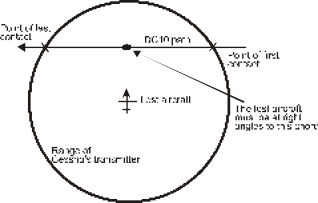 Now that the relative positions of the two aircraft had been established the DC10
pilot flew towards the general direction of the Cessna and recorded the points at
which the Cessna’s radio began to fail. Figure 1 illustrates how, by flying along
a straight line, the DC10 could determine a chord in a circle whose radius is the
200 mile transmission range of the Cessna. The DC10 flies in a straight line and
the point at which the signal is first received and the point at which it is no longer
received defines a chord. The DC10 then reverses track, flies to the center of the
chord and turns at right angles to fly along the diameter. In this way, the Cessna
was located and escorted to New Zealand.
Now that the relative positions of the two aircraft had been established the DC10
pilot flew towards the general direction of the Cessna and recorded the points at
which the Cessna’s radio began to fail. Figure 1 illustrates how, by flying along
a straight line, the DC10 could determine a chord in a circle whose radius is the
200 mile transmission range of the Cessna. The DC10 flies in a straight line and
the point at which the signal is first received and the point at which it is no longer
received defines a chord. The DC10 then reverses track, flies to the center of the
chord and turns at right angles to fly along the diameter. In this way, the Cessna
was located and escorted to New Zealand.
I use this example because it is interesting; students with no knowledge of aviation
can follow it, and it demonstrates sheer human ingenuity. The point I am attempting
to make is that by understanding all aspects of their profession and by thinking
about ‘unusual circumstances’ they are in a better position to solve real-
Aside 1 -
My architecture course covers the data, address and control buses that distribute
information between functional units in a computer. The computer bus provides a fruitful
area for introducing professional aspects as an aside. In a typical computer architecture
course, one of the key aspects of buses that we cover is the protocols that define
their operation. A system with more than one potential bus master must implement
an arbitration mechanism to handle multiple near-
Typical texts describe various arbitration algorithms such as fixed, priority, and
round-
These discussions are intended to illuminate academic points, but they also show students how they will have to make major design decisions and that their decisions may have an effect on society.
Another aspect of buses that can be used to introduce an aside is the notion of standardization; bus protocols, such as the PCI bus, become international standards with documents that precisely define their operational characteristics.
An aside on standardization provides a class with the opportunity to discuss the
benefits of standardization (e.g., inter-
Aside 2 – Overclocking PCs
All digital devices operate in a particular environment defined by factors such as ambient temperature, supply voltage and clock speed. The operating parameters of a particular digital device are determined by its manufacturers and are published as part of its specifications.
A manufacturer guarantees that a component will operate according to its specifications. In general, a digital device will operate somewhat beyond its minimum guaranteed specifications because failure mechanisms are soft rather than hard; that is, as you exceed guaranteed parameters, the probability of failure increases as you move further and further from the standard. In particular, you can operate a CPU at a higher clock rate than its minimum specification.
Because the price of cutting-
In one of my courses I cover memory access times and clocking considerations. As an aside I discuss the notion of overclocking. My students are aware of overclocking and often use it to enhance the speed of their games machines. I ask them to discuss whether it is ethical to operate a computer beyond its design specifications. They invariably say “yes” until I ask them whether they would overclock the computer controlling a nuclear reactor. Overclocking introduces the notion of a designer’s obligation to the community and the need to appreciate failure modes.
Aside 3 – Binary Arithmetic
Some might imagine that it’s difficult to introduce ethical concepts into fundamental topics such as binary number representation and arithmetic. It’s not. One possible entry point for an ethical aside is the impossibility of converting a decimal fraction such as 0.1 into an exact binary representation – and its consequences. Students often find it amazing that there is no exact binary representation of the decimal fraction 0.1. They are even more surprised when I explain how this led to a loss of life.
In 1991 during the first Gulf War, Patriot anti-
This example demonstrates that a failure to understand the implications of a topic as mundane as binary arithmetic can have terrible consequences in real life. I explain that we do not teach binary conversion (and range, precision, and accuracy) simply because it’s there, but because an understanding of these concepts is required by anyone who designs or implements digital systems.
Another aside that could be used when discussing binary arithmetic is the Pentium
bug (an expensive design flaw that cost Intel a lot of money because of a failure
in the implementation of the floating-
Aside 4 – HCI and the Human Interface
Some architecture courses cover input/output devices and I/O technology as well as the CPU and memory devices. Asides that describe the failure of professional responsibilities due to poor interface design in the aviation industry can be introduced via a series of incidents involving commercial aircraft with a major loss of life.
A typical incident that can be used as the basis of an aside is the crash of an A320
Airbus at Strasburg in 1992.[5] On the approach to the destination airport the crew
intended to select a gentle descent with glide slope of 3.3º. The aircraft’s flight
management system operates by inviting the crew to first select the value and then
the units (it’s programmed in very much the same way you program a VCR). Unfortunately
in this case, the unit selected was feet-
The crash involved an error by the crew followed by a failure to monitor the aircraft’s progress (a lack of situational awareness). However, there was also a failure of imagination by the design team who did not anticipate such a problem. Clearly, the two descent modes should have been made more distinct and the crew should have been actively warned that they were selecting a potentially hazardous mode.
The important ethical aspect that this aside is intended to teach is that the designer should be able to identify possible modes of potentially disastrous misuse in the system he or she is designing.
Aside 5 – Instruction Set Design
Another topic that allows me to introduce an interesting aside is instruction set
design, because some engineers have discovered that particular processors will execute
machine-
A computer reads the binary patterns corresponding to machine-
A processor like the Motorola 68K (now renamed as part of the ColdFire family of
embedded processors) deals with illegal op-
Several enthusiasts (in those pre-
The notion of undocumented instructions allows me to ask students whether they, as
future designers, would take advantage of a processor’s undocumented features (this
is analogous to over-
Throughout the life of a processor, the design and organization of a silicon chip may change radically as semiconductor technology and computer organization advances. Consequently, if you write software that relies on an undocumented feature, a later version of the chip may fail because that feature may no longer be implemented.
I tell my students that in the 1980s I once met a professor who knew someone who used undocumented instructions in his work. The work? The guy wrote software for missile guidance systems.
The problem of undocumented instructions is less relevant today because advances
in computer organization and implementation make it impossible for engineers to execute
undefined op-
Aside 6 – Recoding Technology
Computer architecture and organization courses cover storage technologies ranging from static RAM to hard disk to CDs and DVDs. Storage technology, by its very nature, provides an excellent opportunity to introduce several ethical issues such as encryption, security and intellectual property rights.
Recording technologies have given us the ability to store truly staggering amounts
of data in a small volume at a very low cost. This means that a modern large hard-
Copyright issues can be dealt with as a series of topics that cover some of the following issues.
- The significance of modern digital copying technology (digital copying creates perfect copies, whereas analog recording techniques create successively degraded copies).
- The history and ethics of copying.
- The possible abuse of copyright protection by some powerful commercial organizations.
The discussion of copyright can be extended into a debate about the Digital Millennium Copyright Act (DMCA) of 1998 that extends copyright into realms undreamed of by those who originated the notion of copyright. The following points concerning the DCMA are taken from a UCLA website [6] http://www.gseis.ucla.edu/iclp/dmca1.htm where it states that the DCMA has the following implications:
- Makes it a crime to circumvent anti-
piracy measures built into most commercial software. - Outlaws the manufacture, sale, or distribution of code-
cracking devices used to illegally copy software. - Does permit the cracking of copyright protection devices, however, to conduct encryption research, assess product interoperability, and test computer security systems.
- Provides exemptions from anti-
circumvention provisions for nonprofit libraries, archives, and educational institutions under certain circumstances. - Service providers are expected to remove material from users' web sites that appears to constitute copyright infringement.
- Requires that webcasters pay licensing fees to record companies.
The aspect of the DCMA that most affects students is that it is now an offense to
circumvent anti-
Students can immediately appreciate that their own activities could lead them into conflict with the law.
Other possible areas for debate are the potential extensions of the DCMA; for example, analog systems are currently not affected, which means that it is possible to play a CD (or DVD) and capture and record the analog signal. Some would require that an analog signal, corresponding to a watermark, be incorporated within the analog output and that all commercial analog devices (amplifiers, cell phones etc) be designed not to process copyrighted signals. Equally, there have been suggestions that devices such as hard disks should be designed so that they will not store copyrighted information.
All these issues provide extremely useful asides in the architecture class because:
- they relate directly to architecture and recording technologies
- they affect the design and use of system that the students will both create (as professionals) and use as consumers
- these issues relate directly to student lifestyles.
Aside 7 – Patent Law
I was introduced to some of the finer points of patent law when asked to be an expert witness in a legal battle between Intel and the Korean motherboard manufacturer VIA. This made me interested in the theory and practice of patent law and the way in which commercial organizations are able to exploit patent law for commercial advantage rather than using it to legitimately protect an invention.
Most students probably rarely think about patents. This is not surprising because computer architecture text books do not dwell on this aspect of computer design. I explain to students how patents arose and how they are intended to protect an inventor in return for the inventor agreeing to teach the invention by describing it in a publicly available patent.
I explain that students need to be aware of patents. I also point out that patents can, in my opinion, be exploited by using them to prevent a manufacturer carrying out their legitimate activity. For example, a competitor can claim that a company infringes their patent (when there is no real material infringement) and tie up a competitor in legal actions for months. The legal action might require the defendant’s top engineers to appear in court and therefore the legal action becomes a cynical means of delaying a competitor’s innovations.
Student Feedback
The techniques I have described are spread across several courses over different
years of study, ranging from the freshman (first year) to the senior (final year)
student. Feedback solicited from students is both anonymous and non-
However, the feedback I obtain shows two trends. The first trend is that students
feel very strongly about my teaching methods, with some students strongly supporting
them and some opposing them. From the context of the rest of the student feedback
it appears that academically strong and well-
Academically weaker students sometimes appear not to like this approach. They would prefer me to provide only the basic information that they can memorize for the exams.
The second trend is that my approval rating rises dramatically as students progress to their final year. Support for my teaching is usually very strong in the final year. I have tentatively assumed that this effect is due to (1) Final year students are more mature and better able to appreciate the importance of ethical asides and similar approaches to teaching. (2) By the final year, many academically weak students have dropped out.
Conclusions
Embedding ethical and professional considerations in this way has many advantages.
It is an excellent teaching tool because it acts as a buffer between slices of dense
academic material and allows students to relax. It reinforces the material being
taught by providing real-
This paper has provided examples of the use of ethical and professional considerations
in computer architecture topics ranging from buses (the significance of arbitration),
human-
References
[1] The Joint task force on Computing Curricula, “Computing Curricula 2001 – Computer Science” IEEE CS ACM
[2] Hall, S, R, et al, “Adoption of active learning in a lecture-
[3] Stewart, Stanley, “Emergency crisis on the flight deck”, Airlife Publishing Ltd., 1992.
[4] Hayes, Brian, “A Lucid Interval”, American Scientist, Vol 91, November-
[5] Hourizi, R & Johnson, P, “Unmasking Mode Errors: A New Application Of, Task Knowledge
Principles To The Knowledge Gaps In Cockpit Design”, web-
[6] Danielson, Ron, “Copyright and SCU”, Santa Clara University Website, www.scu.edu/staffac/images/CopyrightandSCU.pdf