Malware
This article describes the deadly and devastating malware that acts like a 21st century plague infecting computers everywhere. Malware is a generic term that describes all the software, firmware, hardware, and systems that are either intended to harm a computer system or to degrade its performance. The term malware is derived from the prefix ‘mal’ (in Spanish ‘mal’ means ‘bad’ as in ‘malicious’) and the suffix ‘ware’ (used to mean ‘thing’; as in ‘software’, ‘hardware’, and ‘Tupperware’).
Traditionally, malware refers only to software, but I have extended the definition to include, for example, hardware, because it is possible for hardware to perform the same functions as malware. The subject of malware is included in a course on basic computer hardware and networking because it encompasses both hardware and networking and because it is of prime importance to all computer users and designers. It is one of the areas of computing where even the novice user must have an understanding.
In this article we look at the various forms of malware and discuss ways of preventing infection by malware.
Principal Types of Malware
Before the introduction of the Internet, there was really only one form of malware,
the computer virus. A virus is a computer program that is capable of self-
Prior to the introduction of the Internet, the virus spread, almost exclusively, via floppy disks that were shared between users.
The introduction of the Internet made it possible for viruses to spread via email,
web browsing, downloading programs; etc. Moreover, the Internet saw the development
of new forms of malware such as the worm, a program that replicates over the Internet
and can multiply to such an extent that communication becomes impossible leading
to a so-
Over the past few years, malware has developed considerably both in its sophistication and scope. Once viruses were written by hackers for fun; today, malware is used by criminals to extort money from victims and to perpetuate crime via identity theft and false websites. It has been reported that over 60% of malware is designed to extract money from computer users.
New forms of malware have been developed that are unpleasant rather than deadly; for example, spyware that reports to someone on your use of the computer and browsing habits and programs that modify the way in which your computer operates by changing your browser or search engine.
Malware has even expanded beyond the traditional destruction for fun and criminal
activity into cyberwarfare where malware performs sabotage or espionage on behalf
of governments or organizations. Some believe that complex computer-
Operating systems designers and independent companies have developed software and hardware designed to defeat malware. This has led to a race or competition between software companies and malware writers.
A Short History of Malware
Malware has a long history. However, we can think of it as going through three phases. First came its birth and childhood as it was first thought of as a theoretical concept and then later implemented. Then came its childhood where it grew and various forms of malware emerged. Finally, it matured into something rather deadly and frequently controlled by organized crime.
The theory of self-
One of the first examples of a self-
The first widespread computer virus was developed by Rich Skrenta in 1982. This program was written for the Apple II computer (one of the first popular personal computers) and spread via exchanging 5 ¼ floppy disks. It was written as a practical joke and is now known as a boot sector virus because it is loaded when the computer first boots up. When a new disk is loaded into the machine, that disk too is infected.
The first virus to infect PCs was the Brain virus (also a boot sector virus) released in 1986. This is said to have been written to punish people who illegally copy software. In this sense, it is one of the first viruses specifically written to cause harm.
The tem virus itself is said to have been coined by Frederick Cohen in 1983 because it infects computers analogously to biological viruses. Although virus has become a generic term for all of computer malware today, much malware cannot be categorized as a virus because it does not travel from computer to computer. Today’s malware is often delivered from a central location via email or a web program. Perhaps this should be called vampireware because, like the vampire in literature, it has to be invited in in order to cause an infection.
Another early form of malware is the Trojan horse. This is similar to the virus, but it does not replicate in the same way as a virus. The Trojan horse gets its name from Greek mythology where a wooden horse containing soldiers was left outside the besieged city of Troy. The Trojans pulled the horse into city and during the night the soldiers inside it emerged and opened the city gate to admit the invading army. Trojan horse malware uses a seemingly legitimate program to perform a malicious action.
Trojan horse malware is so names because it shares two characteristics with its mythological counterpart. First, the danger is hidden (like the soldiers in the wooden horse) and secondly, it appears as an article of useful software such as a game or a utility (the Trojan horse was perceived by the citizens of Troy as a gift from the Greeks).
Trojan horse software is widely used nowadays because it has the potential to perform a variety of malicious acts; for example:
Keystroke logging (i.e., recording everything typed into the computer in order to discover passwords and bank details).
Spyware (i.e., reporting back details of your computer such as financial details or shopping or browsing habits).
File browsing (reading your files)
Corruption or destruction of files
Remote control (the ability of someone to take over control of your computer remotely)
In October 1988 a notable virus, the Jerusalem virus, was detected. This was so called because it was first detected in Jerusalem. It was designed to delete all executable files when triggered on any Friday 13th.
The decade 1990 to 2000 saw a steady rise in the number and complexity of viruses and worms. The polymorphic virus was invented to elude antivirus measures. Mark Washburn is credited with the invention of the polymorphic virus, called 1260, in the USA in 1990.
A virus is a program that has a signature (a type of electronic fingerprint), that
identifies it. The signature is some function of the code of the virus rather like
the cyclic redundancy code found in communications systems. To detect a virus, you
scan a computer looking for the signature of a virus. However, the polymorphic (i.e.,
multiple-
In 1995 the first macro virus was created, called Concept. This virus used the macro facilities in Microsoft’s Word. As well as infecting applications, malware writers were able to include viruses in any document or end user software that employed macros (i.e., operations in an applications level program that permit programming). Word macro viruses exploit features of Word to automatically execute malware. The host computer becomes infected and the malware infects the NORMAL.DOT template used by Word to store macros. Once established, NORMAL.DOT will automatically spread to other Word templates.
The macro virus is important because it is spread in the documents you create and distribute. You can disable macro facilities in Word and other Microsoft products.
The situation became worse between 2000 and 2010 with the ever increasing sophistication
of virus, worm, and Trojan horse writers. In particular, large-
Growth of Malware
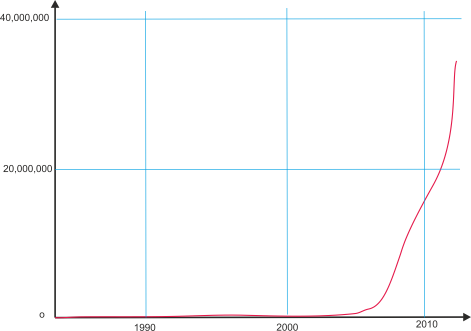
The following graph taken from AV Test data demonstrates the explosive exponential growth of malware. It indicates that malware is a threat that is growing at an exponential rate.
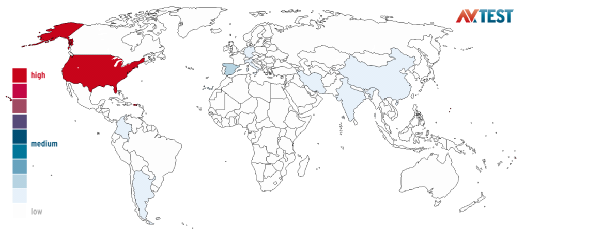
The following figure from AV Test shows the geographic origins of spam over a 180-
Virus Construction
Early viruses were created by what might be called hackers or by academics experimenting with computer software and communications. Such viruses were often created in assembly language.
Assembly language has several advantages over high-
High level languages and scripts make it easier to write malware. Scripts offer many advantages over assembly language and are able to exploit existing operating system functions.
A more sinister form of virus writing mechanism is the virus construction kit; that
is, software designed to enable non-
Virus construction kits were designed with IDEs (integrated design environments) making it possible for anyone to construct a virus with no knowledge of programming or computers. Malware could now be produced by people the way you manipulate images with Photoshop or write documents with Word. Indeed, the term script kiddies was introduced to describe young teens who were creating viruses using kits.
Note that malware itself usually has to leave a marker to indicate an infected system.
Without such a marker, the system could be infected and re-
Virus Transmission
The first malware was spread by means of floppy disks; often when people exchanged programs. Today floppy disks are obsolete. However, the UBS pen drive can easily be infected. I myself had a pen drive that became infected when I plugged it into a conference computer at an international meeting of computer scientists. That was rather ironic! More seriously, the International Space Station, ISS, was infected by malware carried on board by Russian astronauts. Because of this infection, computers on the ISS now use Linus as an operating system rather than Windows.
A common means of transporting an infection is by means of an E-
The sheer flexibility of modern hardware and software helps make computers less secure;
for example, the Unicode character set has a right-
The malware CryptoLocker is transmitted as an attachment to an email. The attachment is a compressed, ZIP, file that contains a filename with the filename and icon disguised. This behaviour takes advantage of Window’s ability to hide filename extensions. For the sake of security, you should turn this feature off.
Sometimes advantage is taken of a specific feature in an operating system. One such source of vulnerability is Window’s registry. The registry is a master directory that contains data that the computer needs to know in order to run programs. For example, the registry stores a program’s settings including its security levels. If malware modifies an entry in the register, it can change the behaviour of the computer.
Classes of Malware
Here we list some of the many forms of malware. Some are very harmful while others merely an annoyance.
Virus
We have already introduced the virus. It’s a program that self-
Trojan Horse
A Trojan horse is a program that appears to be performing a useful function but which is actually performing a hidden illicit function. Trojan horses can install more malware, delete files, or steal data.
Spyware
Spyware is a class of malware designed to obtain information from your computer and send it elsewhere. Spyware may be used by companies researching your viewing or buying habits. It may be used by the authorities to monitor dissidents or the general population. Finally, spyware may be used by criminals who wish to find your bank details and to perform a cashectomony on your account.
Adware
Adware is a form of spoofing in which your browser or similar software is taken over and you are bombarded with unwanted advertizing.
Spoofing
Spoofing or pretending to be something else is not malware in the sense of the virus. It is an attempt by someone to lead you to believe that a network or web page is genuine when it is not. For example, you might be directed to a website that appears identical to that provided by your bank. You enter your name and password in the belief that this indeed the bank’s site.
Phishing
Phishing is pronounced as fishing and it refers to operations that seek to access your bank account details. This is a variation of spoofing and generally refers to emails that take you to a spoofed website of your bank or similar.
Spam
Spam is malware only in the sense that it consumes bandwidth, time (your time to deal with it) and space (memory and disk space. Spam generally applies to unwanted emails. The term spam comes from a sketch by the Monty Python team.
Hoaxes
The hoax is a specific form of spam in which an unwanted email is received promising you riches. This may be in the form of a lottery prize, or an offer of a large sum of cash if you provide them with your bank details so that they can deposit it for you. It is surprising that in today’s cynical world, people can still believe that a perfect stranger will write to them offering to put over ten million dollars in their account.
Scareware
Scareware or rogueware is malware that is designed to change the recipient’s behaviour
by frightening them in some way. For example, you may receive a message saying that
you have a virus or that your system is in some way corrupted, and then you are invited
to buy a product that will fix the (non-
As well as scareware intended to frighten users, there are types of malware intended to get you to do something unwise; for example, information was once distributed that a software upgrade to Apple’s iOS7 would make your iPad waterproof. Some people did indeed fall for this prank and consigned their iPads to a watery grave.
Ransomware
Ransomware is a form of malware that takes control of a computer and refuses to relinquish it until you have paid a ransom. For example, some of your files may be encrypted and you are invited to pay for the key to decrypt your files. If you refuse to pay, you have permanently lost the files. CryptoLocker is one of the most famous examples of ransomware. It appeared in 2013 and it encrypts your data files. You are invited to pay a large sum of money to decrypt your files. If you don’t, your data is lost. A particular danger here is that backup files on the same network may also be encrypted.
Rootkit
The rootkit is a form of malware that is difficult to detect and is a particularly serious form of threat. Here, root refers to the supervisor level and kit refers to a kit or group of malware programs. The rootkit uses these programs to get supervisor privileges and to take over your computer without being detected by users or security monitors. Rootkits can defeat many security products and even change themselves to avoid detection. Even worse, they can turn your computer into a component of a botnet (i.e., a network of infected computers) that sends out further malicious software to other computers.
Worm
A worm is a program that continuously propagates round a network. Some worms include payloads that perform all the same malicious actions as a virus. Some worms simply replicate and propagate to the extent that the network is swamped by worms and collapses. This is called a denial of service attack.
Bot and Botnet
A bot (bot is a shortened form of robot) is a program that infects a computer allowing
it to be controlled remotely. A botnet is a network of computers controlled by bots.
Once your computer has been infected by a bot, it can join the botnet under the control
of a C&C server (command and control). Botnets may comprise 20,000 or more computers.
Members of a botnet can be taken over and used to distribute spam or even pornography.
In 2007 an 18-
PUP
PUP, or potentially unwanted program, has become a generic term for malware and near malware that is often bundled with applications. Anyone who has downloaded a free utility over the Internet will know that the installation procedure may change their default browser, change their default search engine, or install a number of programs that they did not want (such as adware or spyware). Such programs are called PUPs because they are not obvious viruses or ransomware, but their purpose may not be clear to the person that performed the download.
Malware and Crime
Malware was invented by a mixture of academics and computer enthusiasts. It grew and soon attracted a wider base of malista (a malista is someone who designs or deliberately propagates malware). Some malistas are the computing equivalent of trolls who leave negative and destructive messages on websites and bulletin boards; that is they launch malware out of a sense of anger at the external world. Some malistas see distributing malware and creating botnets as a sort of game; they lack the empathy to understand how much harm they bring into the home and office. A third and growing group can be described as criminals. They have no interest in causing harm for the sake of it because they would like to draw as little attention to themselves as possible. The criminal is interested only in making money. Note that here I am excluding the special case of the political activist, cyber terrorist, and government agency who use malware as a means of achieving a specific objective.
Individual criminals send out mass emails (spam) to get their victims to give their bank details by means of, for example, the so called 419 scam where you are told that someone is trying to get money out of their country and they would like to put it in your account and will give you a fraction of the cash if you agree to help. Criminals are also involved with activities such as identity theft and the use of ransomware to extort cash.
The growth of computing, the Internet, the Web, and malware is also attractive to organized crime. Just as business people get together to form companies, criminals have joined forces to create syndicates that perform criminal activities but which are run along the lines of a business. Criminal organizations have advantages over individual criminals in the field of organized crime, because it is possible to separate the malware creation and distribution from the money gathering and the eventual money laundering. In the USA organized crime is often loosely referred to as the mob.
It is interesting that the relationship of organized crime to malware has a precursor. In the early 20th Century in parts of New York a form of localized lottery grew up. This was a simple lottery that involved choosing a three digit number giving you a 1 in 1,000 chance of winning and a payoff of about 500 times your stake money. This was appealing to the poor because they could stake very small amounts of cash. The lottery was known as the numbers game and it was also called the numbers racket. Such highly profitable local lotteries attracted the attention of criminals and many were taken over. The same process is happening with malware.
As an example of the sums involved, it was reported that the CryptoLocker ransomware made over $20 million in the last three months of 2013. However, such figures are estimates, not least because many victims fail to report the crime out of embarrassment. Moreover, banks and financial organizations sometime hide the level of crime in order to avoid frightening their investors.
Spam and adware is probably the most lucrative source of income for organized crime
because it is regarded by the community more as a nuisance than ransomware or identity
theft. McAfee, the anti-
An indication of the hostility to spam is that one of Russia’s most notorious spammers, Vardan Kushmir, was beaten to death and some commentators have suggested a victim of his spamming might be the culprit. However, that has not been established.
Dealing with Malware
Malware can be dealt with at a number of different levels by several agencies. For example; the chip designer attempts to make it difficult for a third party to inject new code into a program by exploiting features of the processor. Similarly, the operating system designer continuously provides software patches to block those who exploit weaknesses in the software.
The computer user, both the individual home user and the professional user must ensure that their computer does not fall victim to malware by implementing a series of carefully considered policies and protocols.
The simplest way to avoid malware is to provide your computer with an air gap. That is, the computer is surrounded by a layer of air and nothing is allowed through that layer (the term air gap really means that the computer is not connected to the Internet or external systems and pen drives and optical storage is not used). If nothing can get through the layer, there is no way that you can become infected by malware. On the other hand, you can’t load new programs, update existing programs, or connect to the internet. This rather limits what you can do with the computer. Such an extreme level of security may be appropriate in safety critical systems such as the computer control of nuclear power plants or aircraft engines.
Is Malware Unique to Windows?
It appears that many people think that malware is a problem that affects only products running Microsoft’s software. Malware can affect any system. Some people hostile to Microsoft have helped encourage the notion that malware is unique to windows, and vendors of alternative operating systems have not always tried to dispel this myth.
Malware is software designed to perform tasks that are invisible to the user. A program you load onto an Apple Mac, a Linux machine, or your Android phone can include malware just as any Windows program can.
However, there are two points to note. First, it is correct to say that some operating systems may be less vulnerable to malware than others. Malware often exploits weaknesses in the code of the operating system in order to embed itself, or to disguise itself, or to propagate. Second, writers of malware wish to target the largest possible number of machines in order to infect the most devices. Clearly, it makes sense to target Microsoft rather than Apple or Android.
I found an article on the web that stated that it was much harder for people to infect Linux systems with malware because of the way in which Linux assigns permissions to files; for example, if you don’t have permission to modify a certain file, any malware will be constrained by the same restriction.
However, the article goes on to state that Windows does have levels of privilege and that harmful operations can be prevented by not running the system in the supervisor or administrator mode. It then says that most Windows users do not have multiple accounts with different levels of privilege and leave Windows to run in the administrator mode. In other words, it appears that some of the difference between Windows and Linux vulnerabilities to malware is due to the relative difference in the sophistication of Windows and Linux users.
Malware and Mobile Computing
Mobile computing using cell phones and tablets is increasing dramatically because
the light-
Many mobile devices use the Android operating system which occupies about 70% of the market. Android is based on Linux and was thought to be relatively safe from attack. However, the growth of mobile computing has caused some malware writers to shift from desktop malware to mobile malware. Kaspersky Lab, a software security company, reported that in 2012 99% of the mobile software they encountered was targeted on Android platforms and that their experts detected over 35,000 malicious Android programs.
A characteristic of mobile computing is the free or very cheap app (application) that is distributed by the million, often by organisations like Google and Amazon. Because it is so easy to write and distribute these applications, they have become a significant threat to the mobile user.
As an example of the spread of malware, SophosLabs’s 2014 Security Threat Report states that ransomware was detected on an Android device in June 2013. The Android Defender malware was designed to make it impossible to access any of the phone’s functions unless you paid a fee of $99.99.
Rules to Live by in an Era of Malware
Finally, here are some general comments on the avoidance of malware. There are three
general groups of rules: education and awareness, the installation of anti-
- User education is everything. All organizations should implement anti-
malware policies and communicate them to their staff. Similarly, home users should appreciate how malware operates, how malware infects a system, and how the system can best be protected. - Read EULAs (End User Licencing Agreements) before installing software to ensure that they are not removing liability for any malware that they may contain.
- Implement a password policy. Report after report indicates that many people use the same password for each application, never change their password, and use passwords like 1234567 or password. Do not use a common word – remember that there are about 200,000 words in English and it is quite easy for someone to run a program that methodically tries each of these words in an attempt to find your password.
- Back up your work and establish a backup regime. It is no good just backing up yesterday’s work because that might have been corrupted and you will be backing up the corrupted versions.
- Install an antivirus program. However, you must appreciate that such programs are not totally effective; for example, they can only guard against virus XYZ after several others have detected it and reported it to the company and they have issued an update to their program.
- Enable a firewall to protect your network ports.
- Ensure that all software, particularly the operating system and anti-
virus programs are up- to- date - Ensure that your software is configured to prevent files from installing and running automatically
- Ensure that macro facilities are turned off in software such as Word.
- Do not open unknown or unexpected email attachments
- Do not click on any banner advertisements that pop up
- Do not forward email with unknown attachments you have received
- Avoid using sites designed to share software such as BitTorrent sites
- If you have to download software, do it from the maker’s own site and from not that of an agent or a distributor.
- Be very careful when handling ZIP (compressed files) because they may contain multiple files in a single archive.
- Avoid pirated software because this is a magnet for malware users.
- Be very careful about sharing flash drives; people share them today like they once shared floppy disks. It is possible to obtain secure USB drives that use either hardware or software encryption techniques to reduce the dangers associated with USB drives.
- Be very careful about enabling remote access. There are many examples of programs and hardware that let you access your computer when you are away from the home or the office. This route can be exploited by others.
Good Intentions Gone Bad
Some security problems are the result of good intentions that turned out, in retrospect, to be flawed.
Autorun was designed to automatically run a program when a CD was inserted. It was implemented at a time when writeable CDs were uncommon and optical storage was used almost exclusively for programs purchased from reputable suppliers.
All you had to do was ‘Pop in the CD and it would run’. However, computer technology developed and USB drives were introduced. Now, malware could be spread by USB drives (pen drives) by exploiting what was once a useful feature.
The USB Drive and Bad Practice
A report from the Ponemon Institute published in 2011 (The State of USB Drive Security
in Europe) presents the results of a large-
Providing employees with approved, quality USB drives for use in the workplace.
Creating policies and training programs that define acceptable and unacceptable uses of USB drives.
Making sure employees who have access to sensitive and confidential data only use secure USB drives.
Determining USB drive reliability and integrity before purchase by confirming compliance with leading security standards and ensuring that there is no malicious code on these tools.
Deploying encryption for data stored on the USB drive.
Monitoring and tracking USB drives as part of asset management procedures.
Scanning devices for virus or malware infections.
Using passwords or locks.
Encrypting sensitive data on USB drives.
Deploying procedures to recover lost USB drives.
Malware and the EULA
When you install an operating system or new software you are almost invariably presented with a EULA (End User Licencing Agreement) that defines the terms and conditions under which you are installing the software.
You have to click a box agreeing to the EULA before the software is installed. Of
course, you first download the full (often multi-
No? I thought not. Admit it, you simply click install without reading the EULA. Consequently, you can find yourself agreeing to quite horrifying terms and conditions.
Companies can include material in the EULA that removes any responsibility for malware in their product or even making you agree to the installation of material that some would consider malware.
The peer-
9.1 During the process of installing Kazaa, you must install software from third party software vendors . . .
9.2 Sharman makes no representations … concerning the … safety … of the third party software …
9.3 There are inherent dangers in the use of any software available for downloading on the Internet, and Sharman cautions you to make sure that you completely understand the potential risks before agreeing to install any of the Third Party Software.
9.4.6 . . . you expressly agree that you accept the Embedded Third Party Software and . . . you will not take any action . . . to disable, remove, block . . . the Embedded Third Party Software.
Here you are agreeing to install unknown software and to run it, and are accepting that Kazaa is not liable for any consequent harm.
The Logic Bomb
A logic bomb is not a form of malware as such; it’s a piece of software that might form the payload of a virus or a Trojan. A logic bomb is designed to perform a malicious act when triggered by predefined circumstances. For example, a logic bomb may perform a malicious act on a certain date such as Friday 13th (the so called time bomb) or it may be activated when, say, disk usage exceeds a certain capacity. The time bomb is sometimes used by disgruntled employees to punish their employers after they have left.
In March 2013 a logic bomb was used in South Korea to erase data on the hard drives of computers at three different banks at the same time.
Virus Killing Virus
Malware is becoming ever more sophisticated. It is possible that some malware may contain within it malware detection and removal programs.
Yes, some malware may detect and remove other malware. Why? Because such malware wants to work on its own. It doesn’t wish to compete with other malware. Moreover, by removing other malware, it helps make the computer look safe to the user.
Symptoms of Virus Infection
Computer users need to know how to detect a viral or malware infection. Unfortunately, not all malware has an obvious symptom. However, here are some possible indications of infection, although many of them may be cause by other factors and no not necessarily indicate a virus. The following list is partially taken from a document by Kaspersky Lab (http://www.kaspersky.co.uk)
Your computer behaves strangely, i.e. in a way that you haven’t seen before.
Your computer begins to run more slowly than before.
You see unexpected messages or images.
Your homepage changes or new toolbars have been added
You hear unexpected sounds, played at random.
Programs start unexpectedly.
Your personal firewall tells you that an application has tried to connect to the Internet (and it’s not a program that you ran).
Your friends tell you that they have received e-
Your computer ‘freezes’ frequently, or programs start running slowly.
Existing functions do not work or appear to have been disabled; for example control+alt+delete no longer opens task manager
You get lots of system error messages.
The operating system will not load when you start your computer.
You notice that files or folders have been deleted or changed.
You notice hard disk access (shown by one of the small flashing lights) when you’re not aware of any programs running.
Your web browser behaves erratically, e.g. you can’t close a browser window.
Java Script
Javascript is a programming language that is frequently used by web browsers to allow
client-
Javascript has been adopted by Adobe for use in PDF documents.
Unfortunately, Javascript can be used to introduce malware; for example, by redirecting web accesses to sites that perform the infection.
Can a Virus Destroy Hardware?
Computer hardware includes all the physical components of a computer, from its case and power supply to the motherboard, CPU, memory chips, buses and storage devices.
Software means programs that can be executed. It is software that can be infected with malware. Once infected, software can act on other programs and corrupt them or cause the computer do perform undesirable tasks such as distribute spam.
So, a computer cannot damage hardware.
Wrong!
Of course, hardware can’t be destroyed by software in a literal sense. But, we live in a world where a lot of hardware is programmable. Software can operate hardware in such a way as to provoke its failure. Consider the jet engine. You can’t be more hardware than that. Jet engines are normally controlled by FADEC (full authority digital engine control) electronics. Suppose malware modified the behaviour of the FADEC to increase the power of an engine to the point at which it would fail after a short period of use; or suppose that the software turned off a lubricating oil pump while reporting back to the pilot that temperature and pressures were all normal?
Similarly, some modern computers allow the internal voltages of the CPU and memory components to be varied as well as clock frequencies. It is not inconceivable that software could not be designed to operate the system in an unsafe condition provoking an early failure. Flash memory such as that used in solid state disks, SSD, had a finite life span in terms of the number of write cycles. Again, software could be developed to continually perform spurious writes to flash memory in an attempt to cause early failure. Even hard disk could be stressed by performing excessive seek operations.
Finally, some systems use programmable and reprogrammable digital circuits. These are complex devices (as complex as a CPU itself) that can be configured electronically; that is, the internal interconnection of gates can be determined electronically. If such devices can be programmed, it may be possible for malware to modify their behaviour.